Network architecture
In this test, we used an ASA5505 as gateway, a Cisco 3750 for the switching and ESXi.
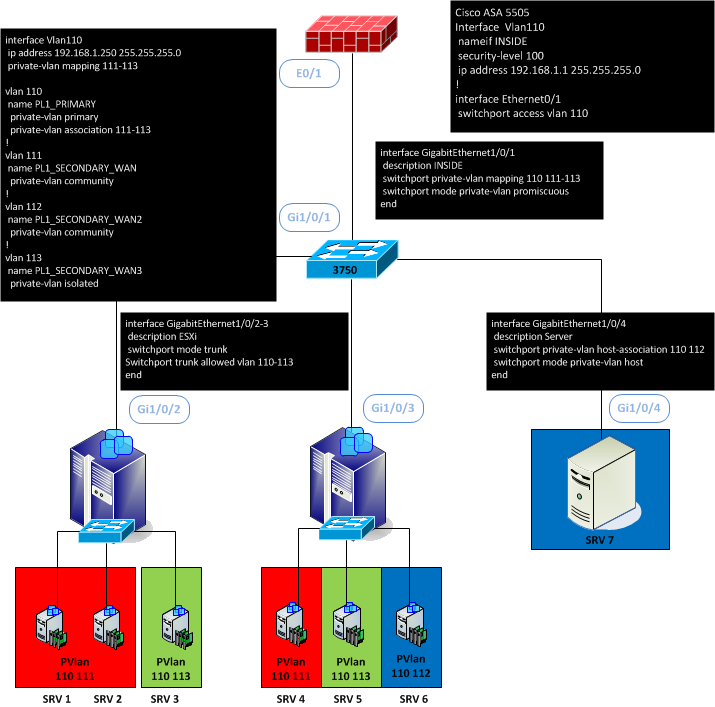
We used 4 Vlans. Vlan110 as primary and 111 to 113 as secondary.
We created a distributed switch on the vCenter and created the private vlans.
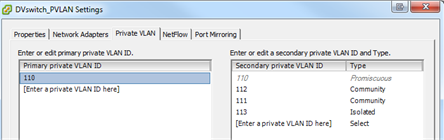
DVSwitch PVLAN Settings
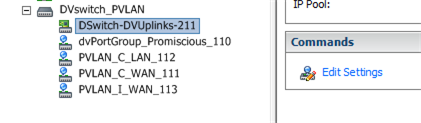
PortGroup List
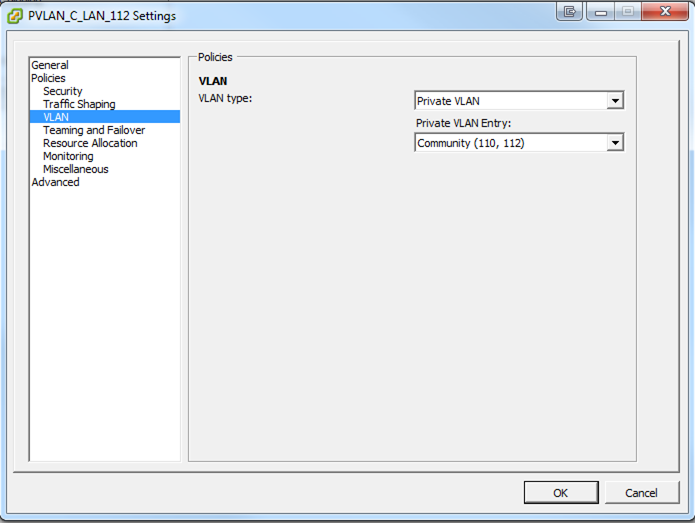
PortGroup Settings
On this plateform, SRV1, SRV2 and SRV4 can communicate together and with her gateway and the SVI, but can’t with SRV3, SRV5, SRV6 and SRV7.
SRV6 and SRV7 can communicate together and with her gateway and the SVI, but can’t with this other SRV.
Finally SRV3 and SRV5 are totally isolated and can only communicate with the gateway and the SVI.
Limitation: With a 3750, you can’t trunk the promiscuous port to a router or firewall tag with 802.1q
With a Nexus some commands have been added.
# switchport private-vlan ? association Private vlan trunk association host-association Set the private VLAN host association mapping Set the private VLAN access/trunk promiscuous mapping trunk Set the private vlan trunking configuration
Now you can trunk your promiscuous port :
# switchport private-vlan mapping trunk ? <1-3967,4048-4093> Primary private VLAN
Now we will try to use PVLAN in promicuous and add a Nexus 3548 with the following version : 6.0(2)A7(1). Before this version, I can’t enable the feature private-vlan.
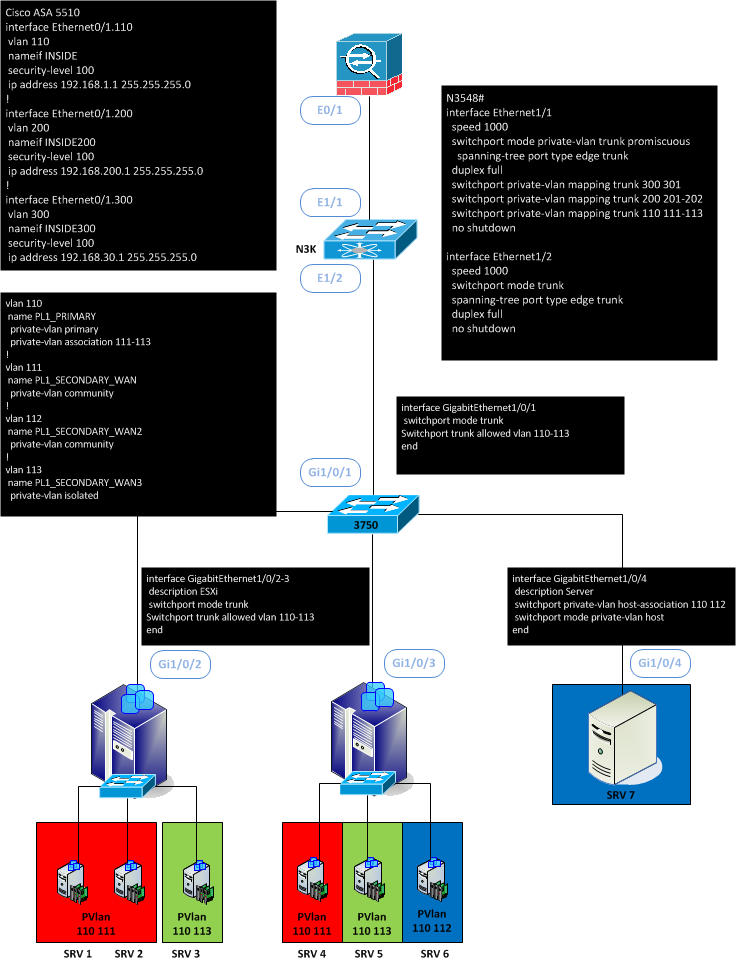
The main difference is the capacity to trunk on the promiscuous port.
interface Ethernet1/1 speed 1000 switchport mode private-vlan trunk promiscuous spanning-tree port type edge trunk duplex full switchport private-vlan mapping trunk 300 301 switchport private-vlan mapping trunk 200 201-202 switchport private-vlan mapping trunk 110 111-113 no shutdown
Here we have three primary vlans (110, 200 and 300) trunked to the firewall.
ASA5510# sh run interface ! interface Ethernet0/0 nameif OUTSIDE security-level 0 ip address 213.218.130.78 255.255.255.0 ! interface Ethernet0/1 no nameif security-level 100 no ip address ! interface Ethernet0/1.110 vlan 110 nameif INSIDE security-level 100 ip address 192.168.1.1 255.255.255.0 ! interface Ethernet0/1.200 vlan 200 nameif INSIDE200 security-level 100 ip address 192.168.200.1 255.255.255.0 ! interface Ethernet0/1.300 vlan 300 nameif INSIDE300 security-level 100 ip address 192.168.30.1 255.255.255.0
Now in the following design, we transport the Private-vlan through a 3750 and we transform the private-vlan isolated 113 to a normal vlan 10. But you can also just terminated with private-vlan.
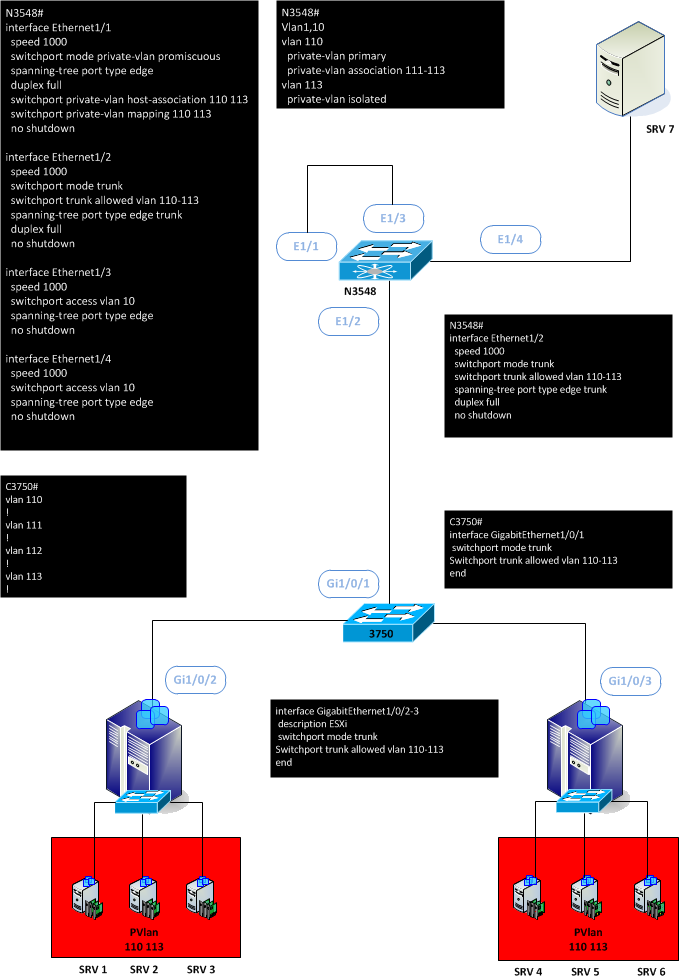
The SRV7 can ping every other servers and the gateway (SRV1 to SRV6), but SRV1 to 6 can’t ping themself except the SRV7.